Solutions Similar Videos
Similar Videos
-
Veritas Direct Migrator
1:32
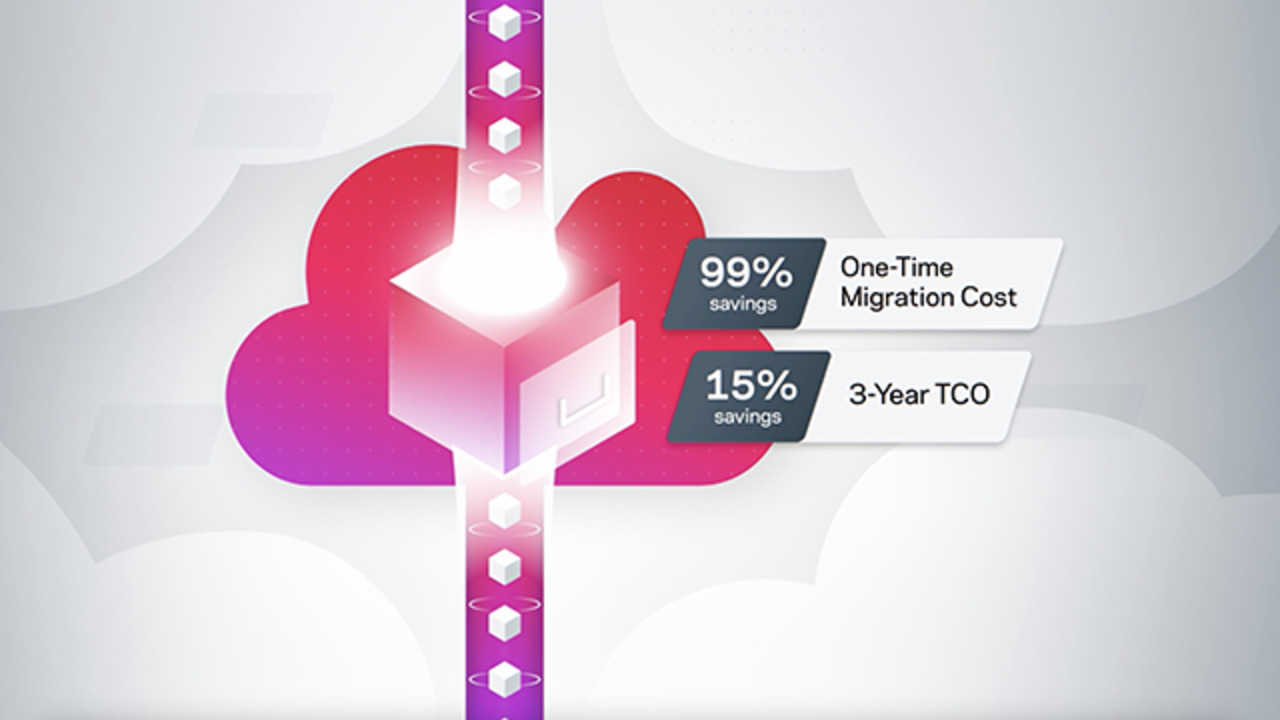
Effortless cloud archive migration. Migrate to cloud archive 5x faster with Direct Migrator. Move data from Enterprise Vault to Veritas Alta Data Compliance with ease and cost-effectively.
-
Veritas Data Risk Solutions
2:17
Veritas solutions are purpose built to address your data risk challenges with a focus on data protection, compliance, and keeping it highly available.
-
Veritas Cyber Recovery Checklist
1:40
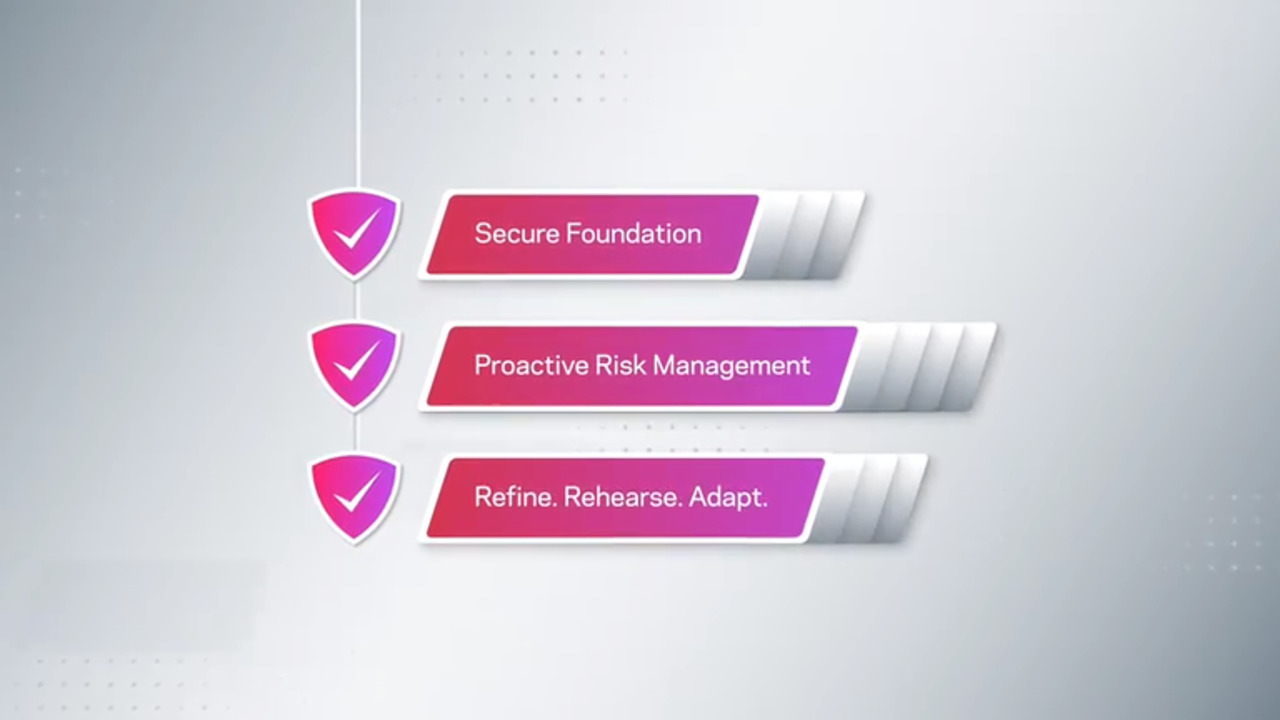
The Veritas Cyber Recovery Checklist is a collection of industry best practices that helps you identify the tools, solutions, and protocols to plan for a rapid recovery in the event of a cyberattack.